DFIR @ Home - Part 1
Investigated a Unifi Threat Management alert for Tor traffic... it was a false positive... sort of...
In summary...
- Working from home, without the aid of well configured security capabilities increases the exposure and susceptability of security incidents. Security controls that are in place within an organisation will provide much better protection that a SOHO or ISP provided router
- Second, in terms of analysis you can not draw conclusions based on only one or two indicators. It's very easy to rush to conclusions and think you are dealing with a compromised machine or a user who had bad intentions, it's always better to do a proper investigation and find out the root cause before taking action.
Also a bit of a disclaimer, all hyperlinks in this post are to legitimate websites, whereas I tried to sanitize the suspicious URLs
Where this started...
I have been receving quite a few adds on youtube for Glasswire, which looks pretty cool for a network monitoring tool, but I think you can already get all of the same data just by using WireShark, so I have decided to look for some other free tools that can do network analytics. After a few searches I came across IPtraf, which is a console application that provides network statistics, google actually pointed me to the following website:
hxxp://iptraf.seul.orgWhen I first visited the website, I saw that the latest version is from 2005, quite old, so I decided its better to forget about this and move on to look for some other alternatives... long story short... Wireshark has a whole menu dedicated to network statistics.
The security alert...
Later on, I saw a notification on my phone from the Unifi Dream Machine which has an Intrusion Detection module. It indicated that someone on the network has done a boo-boo.

After some digging, (as the alert does not include the hostname of the machine) I found out that I was the culprit. I have to admit that in order for me to find out the exact URL I looked through the web history and found the suspicious URL, it looks like I have a lot more to learn about the Unifi network analytics.
The analysis part...
At first glance, it looked like my computer used TOR to browse the internet anonymously, which I know to be false. Next I scanned the website with VirusTotal, which revealed no findings, so what's the catch? I decided to pivot and look for the IP address...
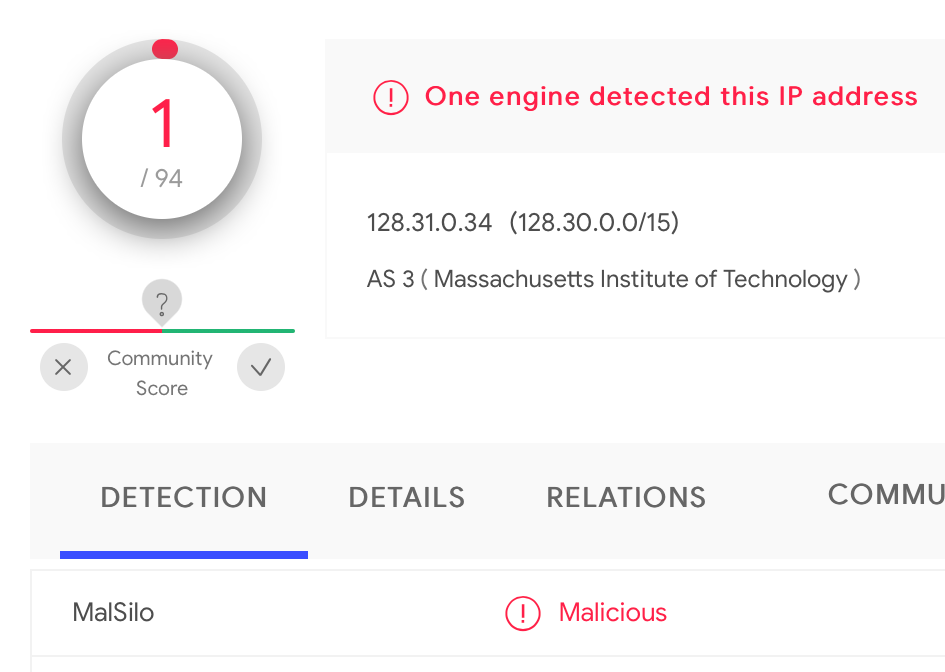
And here is the first hint, at least one engine flags the IP as malicious, there is also a comment that the IP address can be found on pastebin in a dump of indicators of compromise related to Emotet
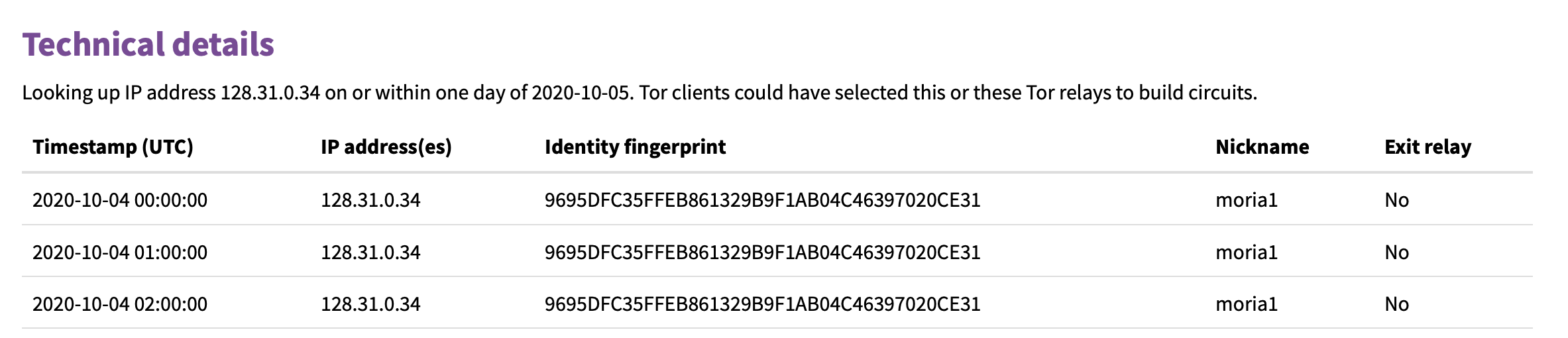
hxxps://pastebin.com/6KRdNNyqChasing another lead, wanted to see if the suspicious IP address is a Tor relay node: https://metrics.torproject.org/rs.html#search. And this proves to be true.
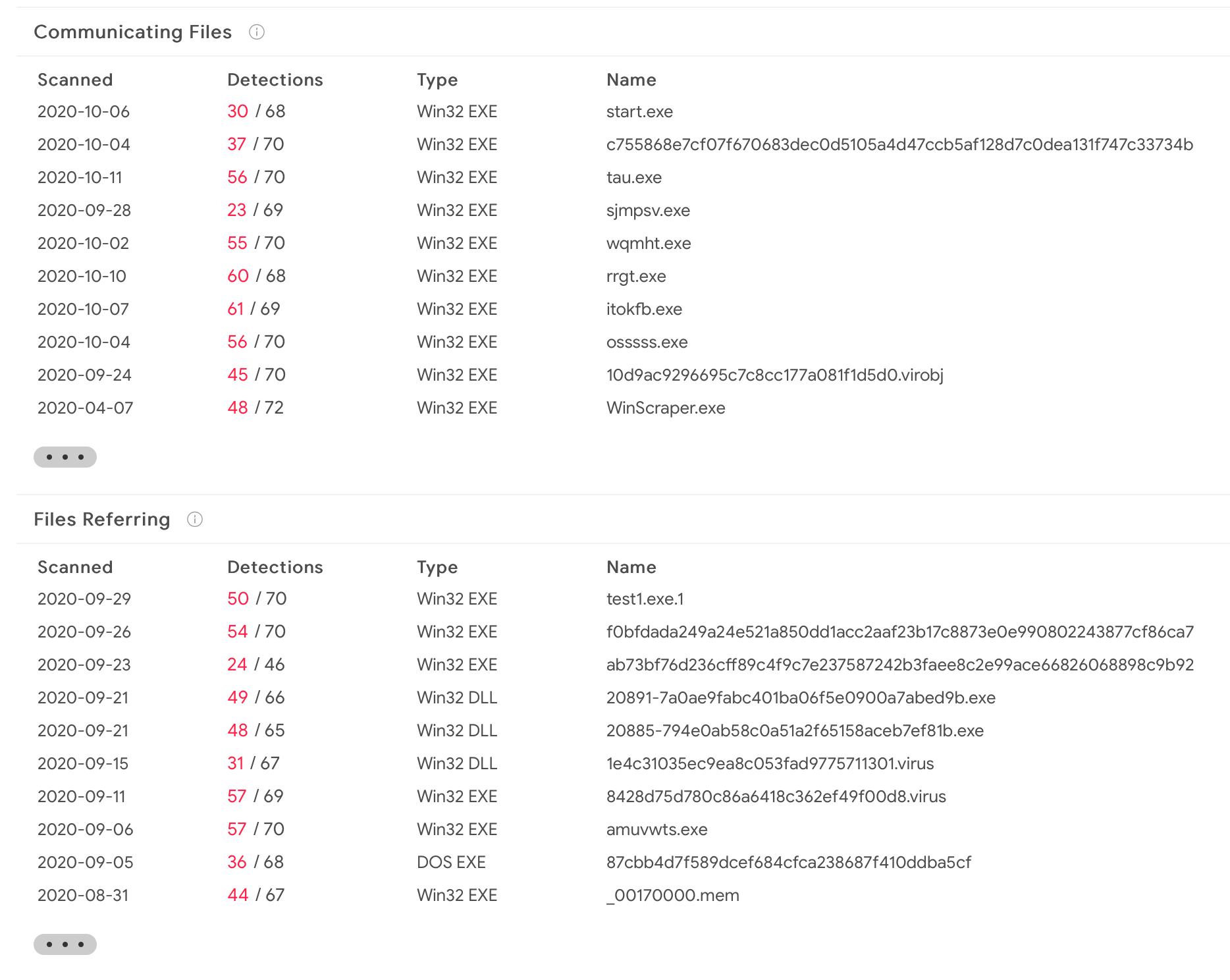
Following the rabbit hole of VirusTotal, I've identified that there are more than a few malware samples that communicate with this IP address or refer to it. Come to think of it, if the malware routes C2 traffic over Tor, it's kind of normal for this to show up.
Calling it quits...
At some point, I decided that this is no loger worth investigating, having concluded that the website I have visited for a tool also is a Tor relay used by malware. The only thing that I've gathered from this experience, is that once again, correlation is really important when conducting analysis. Also there are a lot of things that happen in the background that enterprise grade security capabilities protect you against, whereas working from home you are a bit more exposed... Maybe a good time to refer you to my other article on how to improve the security of your DNS while working from home


