Scanning your home network for vulnerabilities
...A high number of old, unpatched devices connected to your home network might expose you to security threats. In this article we'll explore a very elegant solution to find these vulnerable devices.
Intro
Cloudflare have introducced an open source tool to help with vulnerability scanning, Flan Scan, it's largely based on Nmap with a couple of custom scripts and some nice reporting features.
There are other bespoke tools such as OpenVas and Nessus Essentials but these can become a bit challenging to set up, configure and run, these are not known by everybody. Nmap on the other hand has been used not only by the security community but has been embraced by the IT community as a whole.
Personally I don't run this on a periodic baisis, but I think even running it once on your home network, you will find some interesting things, especially around IoT and maybe your router/modem provided by your ISP.
Getting started with Flan-Scan
Leveraging Docker
The only requirement to successfully run this tool is Docker. And this makes it quite flexible in terms of deployment options:
- If you have a RaspberryPi you can install docker and run it there
- Docker in a Linux VM
- Docker on Windows (or install via WSL2)
- Docker on Mac
I have some other small and interesting projects in the pipeline, so it's very good to get familiar with Docker.
The good part is that after installing Docker, you need to donwload flan-scan or clone it from the official GitHub repo and build it:
git clone https://github.com/cloudflare/flan.git
make buildYour first scan...
Before running your first scan you need to specify with IPs or IP range(s) it should scan. This can be done my edditing the /shared/ips.txt file. You can add specific IP addresses one by one, or you can add the range using the CIDR notation.
The default scan reports are genrated using LaTeX, I have a lot of respect for people who are proefficient with it, but I'm not a huge fan as I prefer Markdown.
Anyways, getting back on track, running your first scan:
make htmlOne command, it's that simple. You can do a bit more tinkering with the commandline parameters.
The project is quite well documented and I haven't run into any issues. More details can be found at: https://github.com/cloudflare/flan
Some interesting findings...
To extend the range of my Wifi, I used an Ubiquiti airCube, well this has a vulnerability within the DNS service, and to be honest I have not enabled this when configuring it, so quite an interesting find.
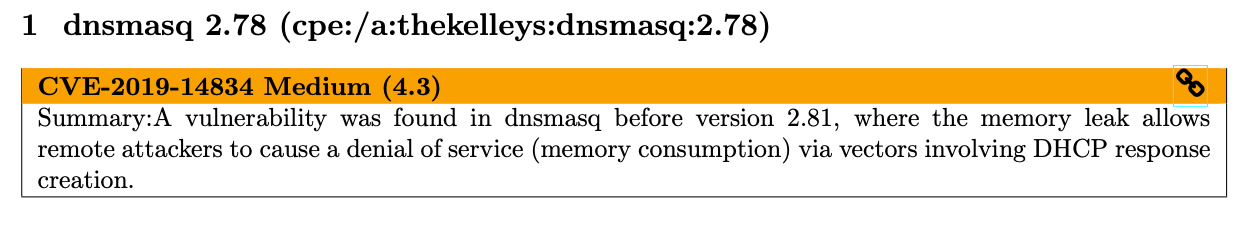
While many of my other devices where ok, including NAS, printer, thermostat, etc. the biggest surprize was actually the router/modem provided by the ISP:
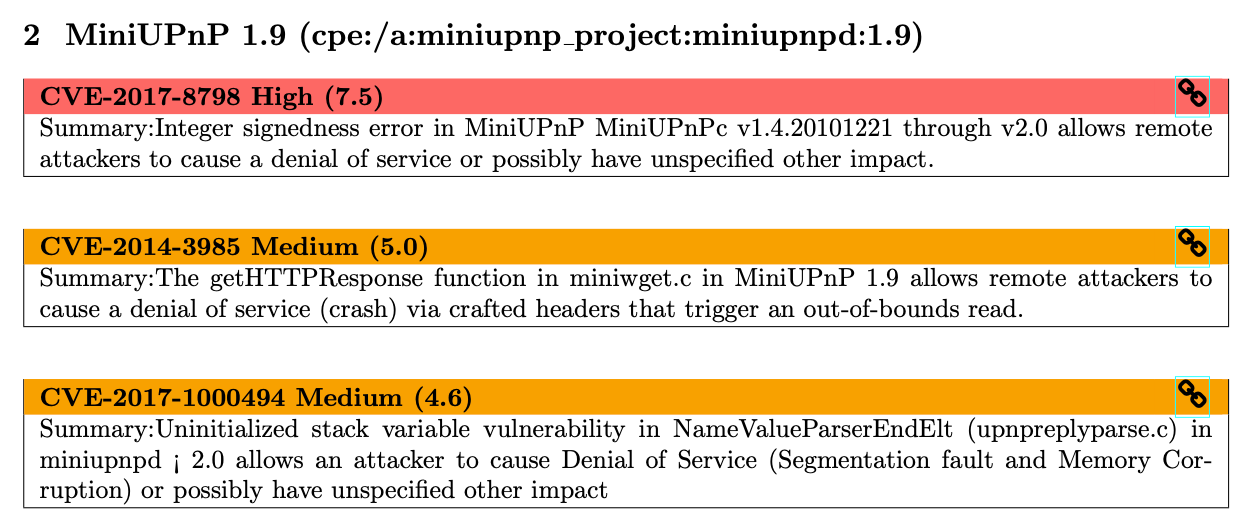
The interesting part is that this device is managed by the ISP, there is no "button" for me to press to update it.
While this looks bad, the next set of findings against my Synology NAS were quite quite impressive:
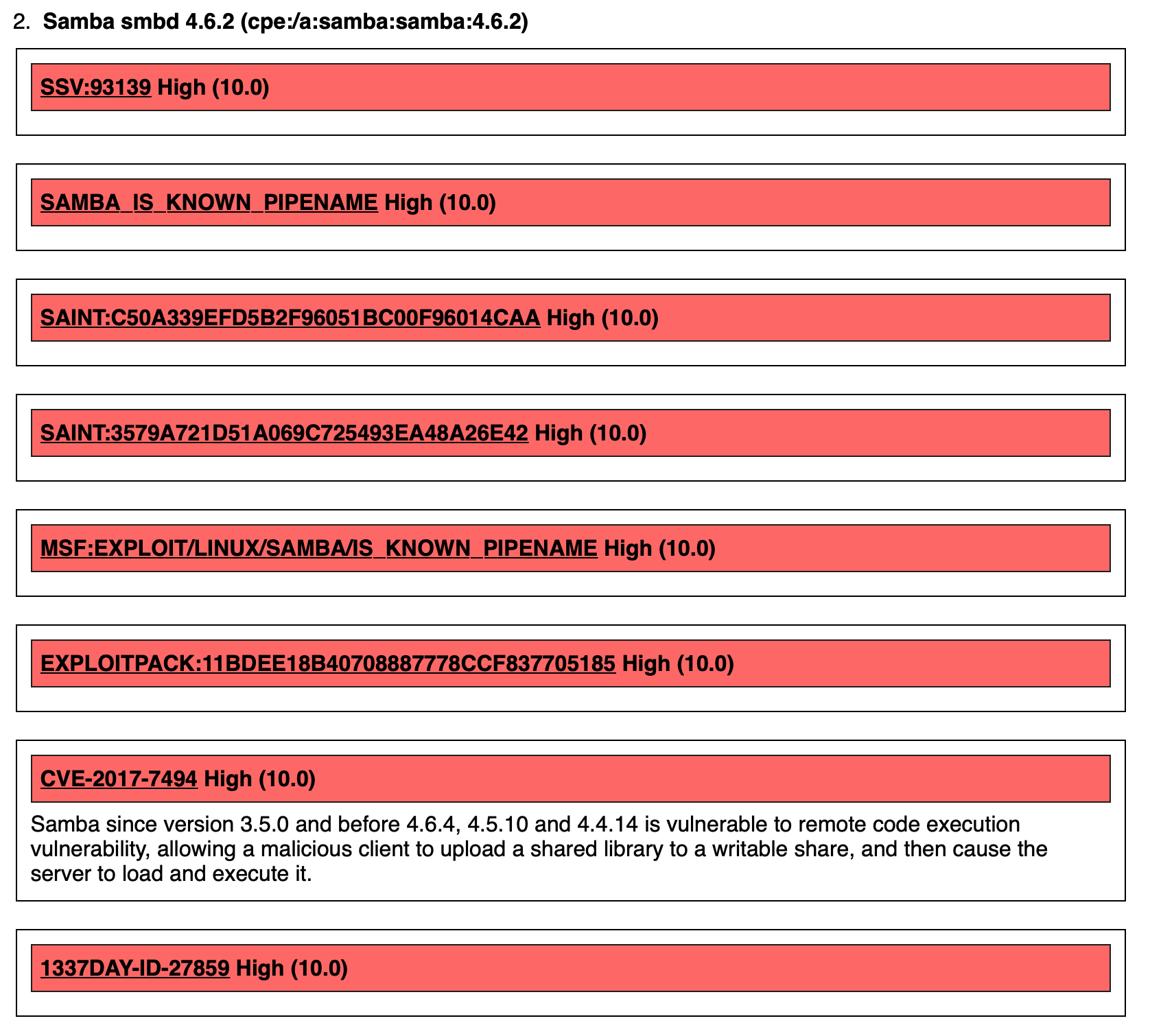
Yes, this looks bad, but even more concerning is that the NAS is actually up to date.
I did some more digging on this, and at least for CVE-2017-7494, there is a fix and maybe the finding is just a false positive.

Probably the easiest would be to disable SMB and only use the other file sharing services. I did some research and found out that Synology NAS units were targeted by Ransomware. Luckly, my NAS is not accessible from the internet... I actually verified it to be sure.
The moral of the story...
It's better to identify these kinds of things early on before risking data loss or having some of these vulnerable devices getting infected and spreading malware to your other devices on your network.
Alternatives...
Flan Scan is not the only solution to carry out these kind of routine scans. at it's core it runs Nmap with the vulners script which has a bunch of signatures to identify vulnerabilities. Flan Scan is just a wrapper which makes it easier to execute and create a report, you can run Nmap independently and configure it to your heart's content.
Google Tsunami...
Another great tool which I have discovered is Google Tsunami. This looks like on awesome tool, it's more of a scanning engine that leverages plugins. I haven't played with it yet, but definetly I think it's a nice subject for another post.

